Setting up Corporate Login/SSO for TrueContext using Okta
Available on the Enterprise tier only:
Contents
About
This article is specific to configuring Okta as a corporate login identity provider (IdP). It expands on what is discussed in the general corporate login article here.
Setting up Okta for use with TrueContext
Follow the steps below to set up Okta for use with TrueContext.
To support existing integrations, some items will continue to use “prontoforms” or “pf” in the domain or code.
For more detailed information about what’s changing, visit https://support.truecontext.com/hc/en-us/articles/19516168513556
Create an Application in Okta
- Set the Platform to "Web"
- Set the Sign on method to "SAML 2.0"
- On General > App Settings, specify an Application Label (for example, TrueContext).
- In the Configure SAML Settings:
- Single sign on URL =
https://live.prontoforms.com/saml/SSO - Check "Use this for Recipient URL and Destination URL"
- Audience URI (SP Entity ID) = prontoforms.com/prod
- Application username is typically set to Okta username or email, but this is based on your specific configuration. In general, you need to specify the setting here such that the username returned by Okta will match the username in live.truecontext.com
- You will end up with something similar to:
- Single sign on URL =

Download the Identity Provider (IdP) Metadata from Okta
- Download the identity provider metadata xml from Okta by selecting the Sign on tab, then select Identity Provider metadata:

-
Save this file for use in the next section.
Set Up Corporate Login in TrueContext
-
Within live.prontoforms.com, navigate to the security tab and select Update within the Single Sign-on menu:
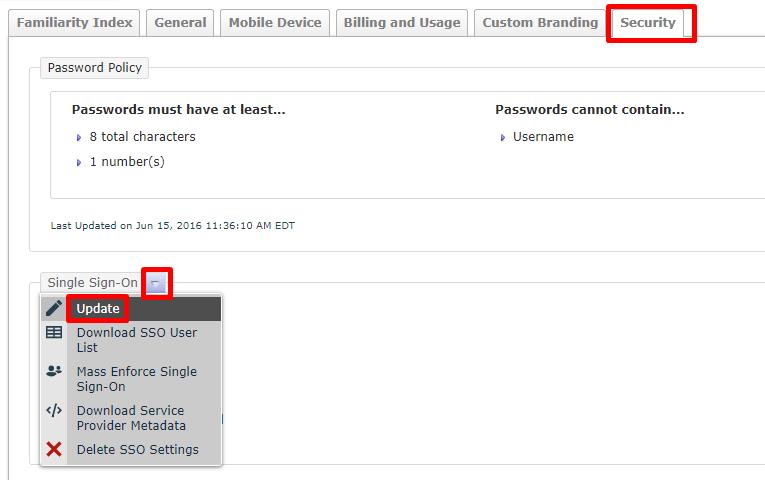
-
Provide a Team domain name. This is typically just your corporate domain name.
-
Specify a problem contact email
-
Optional: Specify a Username suffix. This is only required if you need to add a suffix to the username returned by Okta so that it matches the username within live.truecontext.com. As an example, if Okta is configured to send just the username prefix (for example, jsmith), but the TrueContext username is jsmith@acme.com, specify @acme.com as the username suffix. However, if Okta is configured to send the username as the user’s email address, and the TrueContext username is also the email address, leave the Username suffix field blank.
-
Select Choose File under the Identity Provider Metadata section and select the file downloaded from Okta in the section above.
-
Select Update.
Tip:At this point, you’ve completed the setup of Corporate Sign-On using Okta. If you need help because of an error or other issue, review the Technical Support Handbook before you contact Support. The handbook describes the information that the Support team needs from you.
Allowing the tile in Okta to login to TrueContext
Currently, TrueContext only supports the SP initiated flow of logging in, and not an IdP initiated flow. This means that the user must initiate the login process by going to TrueContext (either via the app or live.truecontext.com in a browser), choose Corporate Signon, and enter their username or team domain to initiate the correct login flow. Simply clicking the SAML TrueContext app tile in Okta will result in an Access Denied error.
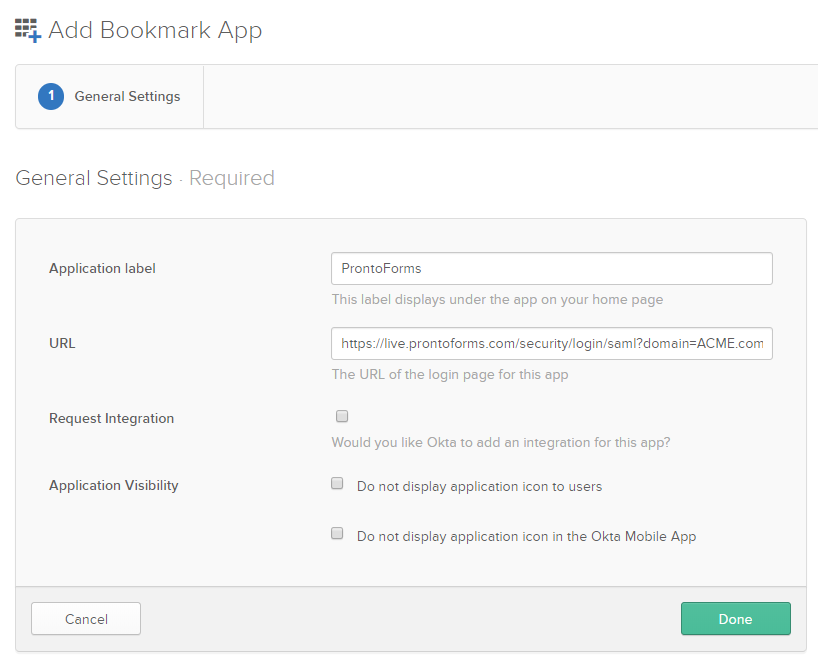
A workaround for this is available by creating a second TrueContext tile (Bookmark App) in Okta.
For the bookmark app to work, specify the URL as:
https://live.prontoforms.com/security/login/saml?domain=<SSO team domain>
Once this is in place, you can hide the SAML TrueContext app from users view in Okta to avoid confusion.