HIPAA Compliance and Security Features
Contents
Introduction
The Health Insurance Portability and Accountability Act (HIPAA) is a United States federal law designed to protect the privacy and security of patients’ sensitive health information. TrueContext offers configuration options to help covered entities![]() An entity is a category in a form, an asset, site, project, customer, person, or product, that identifies who or what a form is about. meet their HIPAA compliance requirements. TrueContext undergoes an annual SOC 2 and HIPAA Security Rule audit by a third-party to attest to the suitability of the design and operating effectiveness of our controls relevant to security, availability, and confidentiality.
An entity is a category in a form, an asset, site, project, customer, person, or product, that identifies who or what a form is about. meet their HIPAA compliance requirements. TrueContext undergoes an annual SOC 2 and HIPAA Security Rule audit by a third-party to attest to the suitability of the design and operating effectiveness of our controls relevant to security, availability, and confidentiality.
Recommendations and best practices
TrueContext helps support your HIPAA compliance, but using the TrueContext service does not on its own achieve it. Your organization is responsible for ensuring that you have an adequate compliance program and internal processes in place, and that your particular use of TrueContext services aligns with HIPAA and the HITECH Act. The following sections provide recommendations and best practices for configuring TrueContext to maintain HIPAA compliance.
Implement robust internal controls
Implement robust internal controls regarding general TrueContext system access and system usage.
| What TrueContext Does | Recommendation | Useful Links and Notes |
|---|---|---|
|
TrueContext provides the ability to:
|
Configure your password policy or authentication scheme to comply with HIPAA requirements. | |
| User accounts will be locked automatically after five failed login attempts, which prevents the user from logging in, accessing, completing, or sending forms. | No action required. | |
| TrueContext provides the ability to configure a maximum session length, after which users will be forced to reauthenticate. | Configure the maximum session length per your organization’s policies and HIPAA requirements. | Session Length |
| TrueContext offers three different user roles (Mobile-only User, User, and Admin). We also provide the ability for your organization to assign users to groups that have permissions to view selected forms or FormSpaces. |
Note:User accounts are intended for use by employees of covered entities; they should not be provided to patients who have rights under HIPAA. Customer Feedback Forms |
Remove user accounts
Remove user accounts for users who have been terminated.
| What TrueContext Does | Recommendation | Useful Links and Notes |
|---|---|---|
| TrueContext provides the ability for customers to configure user permissions and remove users. | Manage and delete user accounts based on your organization’s policies. | User PermissionsManage User Accounts
|
Protect data during transmission
Protect data being transmitted to and from the TrueContext system.
| What TrueContext Does | Recommendation |
|
|---|---|---|
|
Data within the TrueContext system is encrypted in transit and at rest. Data transmitted between mobile applications uses TLS 1.2 or higher encryption. Data stored on our servers is protected using AED-256 encryption. Data stored on mobile devices is protected using native encryption provided that a passcode is enforced. |
|
Enforce a Passcode |
| TrueContext servers are hosted by AWS and located in the United States. When Data Passthrough is enabled, no submitted form data will be saved in the TrueContext system – only a record of where the data went. Enabling this feature may limit TrueContext Support in their ability to assist you. |
If desired, enable Data Passthrough for forms that contain sensitive information. |
|
| With the recommended Form Settings configured, images captured in the Mobile App are not saved to the user's camera roll. All images and signatures are deleted from the device once the form is successfully submitted and processed. | Make sure the option to save images on devices is not enabled. | Image Options |
| With the recommended Form Settings configured, users are unable to save, print, or share a PDF summary of the form. |
Make sure the option to share the Summary Page is cleared. |
Summary Page Options |
| TrueContext provides the ability to customize how long completed form submissions are stored in the Sent box on mobile devices. |
When configuring your forms, enter “0” to disable the storage of form submissions in the Sent box. This ensures that no part of the form remains stored on the device. |
Sent Box Options |
| TrueContext provides the opportunity to configure Data Destinations if desired. |
Bear in mind your compliance requirements when configuring Data Destinations. Include only the destinations that are needed and ensure that your destinations have adequate safeguards in place to meet your compliance needs. Using email destinations is generally not recommended. Perform an assessment of the security controls of the cloud storage provider or content management service for its suitability for use in healthcare. Cloud storage services should only be used if a business associate agreement is entered into with the service provider. Note:A cloud service that claims to support your HIPAA compliance can be used in a manner that violates HIPAA rules, as HIPAA compliance depends on the people that use the product or service rather than the product or service itself. |
Creating and Managing Data Destinations Note:TrueContext is not responsible for the security practices of third-party organizations who provide Data Destinations. You must verify that a Data Destination If you have HIPAA compliance requirements, you should not use Email or SMS Data Destinations. |
Implement a business continuity and disaster recovery plan
| What TrueContext Does | Recommendation | Useful Links and Notes |
|---|---|---|
| TrueContext maintains an SLA of 99.5% uptime. We back-up your data to our disaster recovery region daily and simulate disaster recovery quarterly. | Implement your own Business Continuity and Disaster Recovery plan for other aspects of your business. Subscribe to TrueContext Status page updates. | Status page |
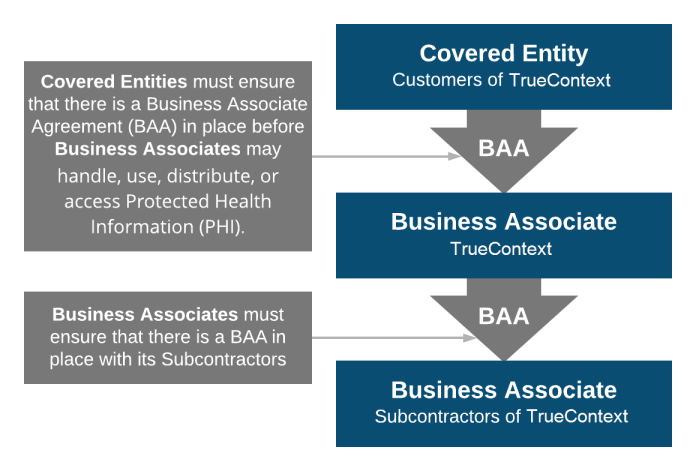
Considerations for Covered Entities
Business Associate Agreements (BAAs) are mandated by the HIPAA Security Rule. BAAs consist of information regarding the permissible and impermissible uses of PHI between two HIPAA-beholden organizations. That can include relationships between a Covered Entity and a Business Associate, as well as relationships between two Business Associates.
For more information on putting a Business Associate Agreement in place with TrueContext, please contact infosec@truecontext.com.
For more information, refer to the following topics: